Once upon a time…
Once upon a time when we would create a user account we would store the password in what we call plain text. This means that it took no other measures to read the password once you found it. Imagine that I kept a list of usernames and passwords hidden in a book on my bookshelf. If you found the book, and subsequently the password list, you easily had everything you needed. The hard part was finding out where the password list was stored.
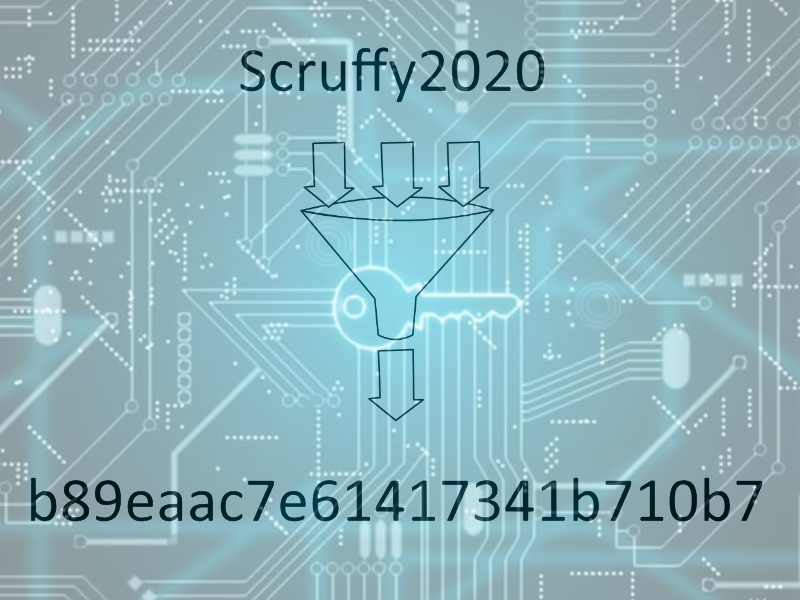
Now a days any entity worth their salt hash passwords. This is a key point… any company storing passwords should be hashing them. This technology is not new and should be mandatory. The picture above gives an example of the password Scruffy2020 being hashed into b89eaac7e61417341b710b7. This is the result of producing a one-way hash. This means that you cannot figure out the password, Scruffy2020, by analyzing the hash b89eaac7e61417341b710b7… it is impossible… more on this in a minute.
Using hashed passwords means that actual passwords are never stored. When you create your user account and provide a password, the password is ran through an algorithm that produces a one-way hash. It is the hash value that is stored, not the password. The next time you go to log in, the password that you supply is hashed and that hash value is compared to what was saved when you created your account. If the 2 hash values match then we know that you have entered the correct password.
One-Way Hashing
Let me give you a very simple example of a one way hashing algorithm using the password Scruffy2020.
Step 1 – I will require your password, when you are creating it, to be at least 3 characters long. I’ll take the password and repeat it 10 times and then I’m going to grab the first 28 characters. I’m going to do this because when I am done hashing I want the resulting value to be 14 characters long… all the time… no matter how long the original password was. This way you have no idea how long the original password was. You’ll see how we get to 14 characters in a second.
Scruffy2020Scruffy2020Scruffy2020Scruffy2020Scruffy2020Scruffy2020Scruffy2020Scruffy2020Scruffy2020Scruffy2020
Step 2 – I’m going to use a simple one letter substitution… a = b, b = c, A = B, B = C, 1 = 2, 2 = 3, etc.
Scruffy2020Scruffy2020Scruff turns into Tdsvggz3131Tdsvggz3131Tdsvgg
Step 3 – I am going to remove every other character. Because I am removing every other character you cannot reverse this process… you don’t know what the missing characters were.
Tdsvggz3131Tdsvggz3131Tdsvgg is now Tsgz11dvg33Tsg
My resulting hash is Tsgz11dvg33Tsg and is 14 characters long. That is the value that I will store as your password instead of Scruffy2020. Every time you log in and enter your password I will take the password entered and run it through the 3 steps above… I will take the resulting hash value and compare it to what I have stored. If they match then I know you entered the correct password.
If you steal, or otherwise obtain my password list all you are getting are password hash values. Let’s pretend you did that… you stole my list. For the account we’ve been using you have the password hash of Tsgz11dvg33Tsg. Let’s try and use that hash,Tsgz11dvg33Tsg, to log into our account.
Step 1 on the value of Tsgz11dvg33Tsg will result in Tsgz11dvg33TsgTsgz11dvg33Tsg
Step 2 will result in Utha22ewh44UthUtha22ewh44Utg
Step 3 will give us Uh2eh4tUh2eh4t
Thus the new calculated value of Uh2eh4tUh2eh4t does not match our stored value of Tsgz11dvg33Tsg. You are not getting in.
Hopefully at this point you can see that you cannot reverse engineer this process to determine the original password. As such, be very concerned if you click I forgot my password and they can send you your original password. This means that they are storing your original password somewhere.
Extra credit reading
There is a thing called Security Through Obscurity where a large part of the security of something is in keeping a secret and making sure that secret stays… secret. Let’s pretend that we actually wanted to use the algorithm above to generate hashes. One of the flaws of this notion is that we’d have to keep this algorithm a secret. If the algorithm got out then people would be able to hack into our accounts pretty easily. Keeping it a secret could be difficult. People could stumble across the algorithm or employees could share the algorithm (on purpose or accidentally) with bad guys.
Many proper hashing algorithms exist such as SHA-256, RipeMD, MD5, etc. are much more complicated and secure than our example. Their formulas are not secret and widely available for people to test and try to hack and they have proven the test of time to be very good.
